
I and my colleauge Onurcan Akıncı completed an Industry 4.0 senior design project on 2017-2018 fall and spring terms in ITU with precious advisory and great support of Dr. Ali Fuat Ergenc. We were both students in ITU Control and Automation Engineering Department, with in passion to do cool stuff. Here is our story of achieving the success in connecting different kinds of industrial equipments to cloud and performing POC’s of Industry 4.0 scenarios on it.
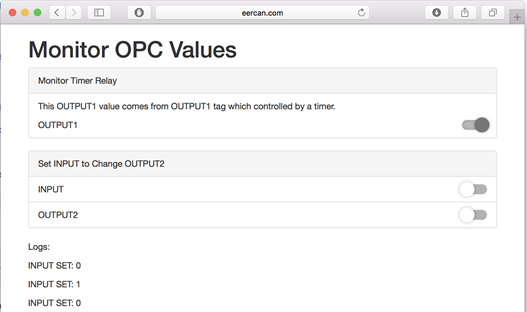
Connecting an industrial equipment to a cloud platform offers endless possibilities of data processing and integrations. This tutorial aims to connect an Allen-Bradley PLC to cloud. We’ll do it on a legacy PLC which has OPC-DA protocol. We need to pull and push data from OPC-DA to MQTT to be able to benefit cloud resources on an industrial equipment. Let’s see.

What is Reference Architectural Model Industrie 4.0 (RAMI 4.0)? You’ve come across with RAMI 4.0 because it’s started to being used as a service-oriented architecture for Industry 4.0 projects. Reference Architectural Model Industrie 4.0 is a three-dimensional map showing how to approach the issue of Industrie 4.0 in a structured manner.
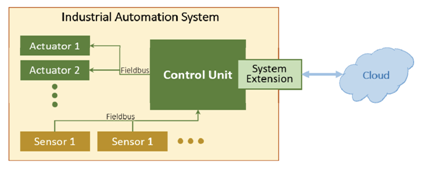
The term Industry 4.0 comes from a combination of major innovations in the digital technology and hardware automations. But have you ever heard of cyber-physical systems? Probably not, because it’s not much populer in marketing presentations; you can come across with it at papers, mostly. Let’s have a look at them.




